1. Why the Bill?




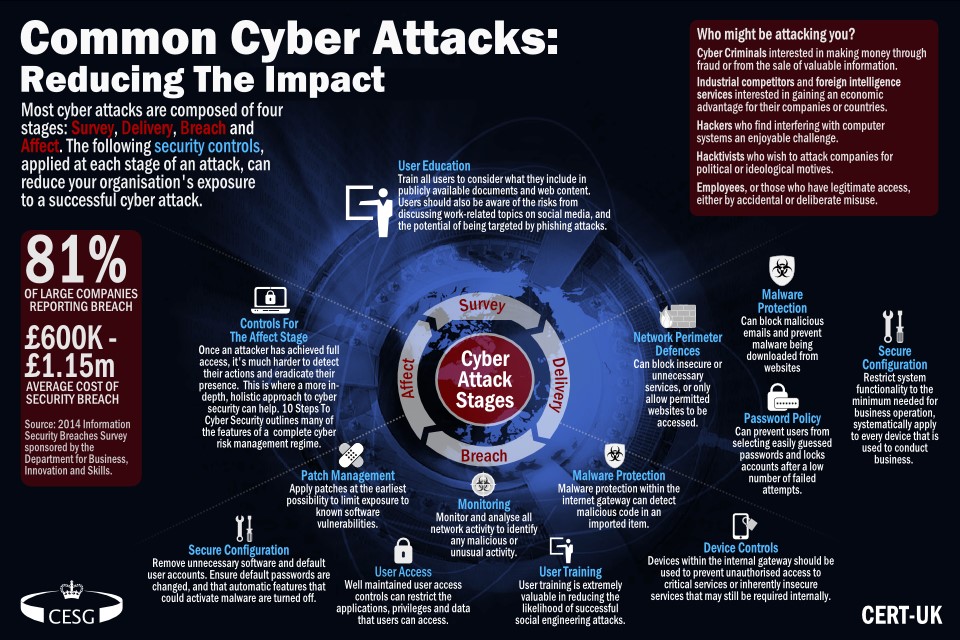
- The UK government states that the digital economy and essential public services are increasingly under threat from cyber-criminals and hostile state actors. (GOV.UK)
- Existing key legislation — namely the Network and Information Systems Regulations 2018 (NIS 2018) — is judged by government reviews to be insufficient for current threat levels. (GOV.UK)
- Major incidents (e.g., the NHS, defence sector, supply-chains) underscore the urgency. (GOV.UK)
- The policy statement emphasises that cybersecurity is not just a cost or compliance burden — it’s a foundation for economic growth, innovation and resilience. (GOV.UK)
In short: The Bill is driven by a recognition that cyber-threats are evolving fast, many organisations are under-prepared, and the regulatory framework needs updating to match the pace of change.
2. What the Bill does — key measures

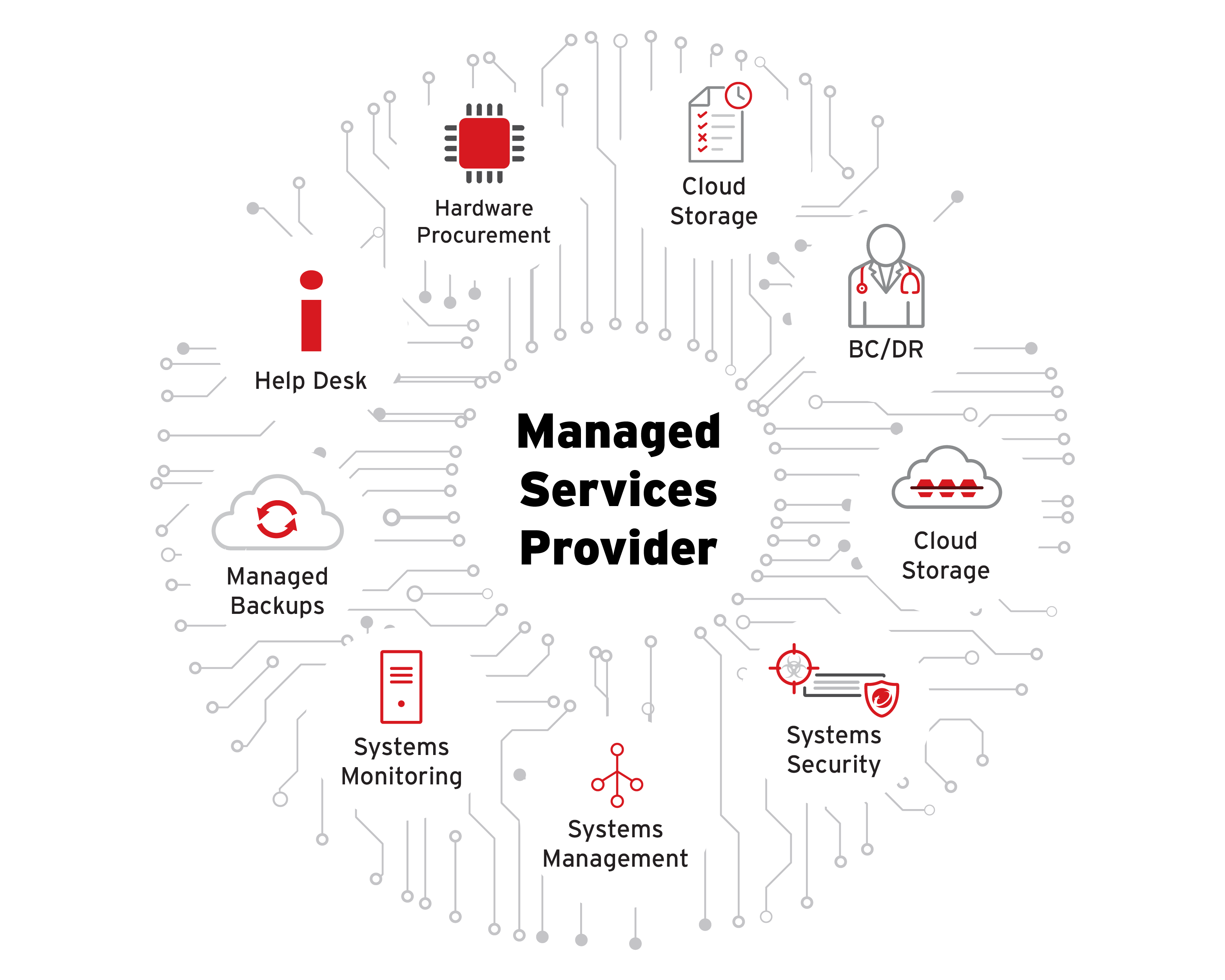

According to the official policy statement and supporting documents, the Bill will bring a number of significant changes. Here’s a breakdown:
A. Expanding the scope of regulation
- More entities will fall under the regulatory regime. For example, the Bill will expand beyond traditional “operators of essential services” (OES) and “relevant digital service providers” (RDSPs) to include more digital supply-chain firms, managed service providers (MSPs) and critical suppliers. (GOV.UK)
- The idea is to recognise that many high-risk vulnerabilities lie in the supply chain, or in firms that provide trusted access to critical infrastructure. (GovNet Blog)
- For example the policy statement estimates “securing a further 900-1,100 MSPs” under one piece of the expansion. (GOV.UK)
B. Strengthening supply chain and designation powers
- The Bill will allow the government (through secondary legislation) to designate “critical suppliers” in the supply-chain of essential services / digital services. These suppliers will then have security-duties similar to the main operators. (GOV.UK)
- The rationale: a weakness in a supplier can ripple through and affect core services. (GOV.UK)
C. Empowering regulators & oversight
- Regulators will be given stronger powers, including cost-recovery mechanisms (i.e., charging the regulated firms for oversight) and proactive investigation powers. (GOV.UK)
- The Bill will enable the Secretary of State to update regulatory frameworks and add new sectors without needing fresh primary legislation each time — making the regime more adaptive. (GOV.UK)
- There may be a new requirement for the Secretary of State to publish a “Statement of Strategic Priorities” for cyber regulators (to ensure alignment across sectors). (GOV.UK)
D. Incident-reporting and transparency
- The Bill will revise the incident-reporting regime: expanding the kinds of incidents that must be reported, shortening reporting windows, and streamlining how reports are made. (GOV.UK)
- Although the precise thresholds and windows are still to be legislated, commentary suggests something like “within 24 hours” notification of a significant incident, then fuller report later. (Reddit)
E. Technical/security requirements
- The Bill will allow for the creation or updating of technical security standards for firms in scope — through codes of practice, regulated duties, etc. (Consultancy.uk)
- For example, firms may need to implement security measures in line with the National Cyber Security Centre (NCSC) Cyber Assessment Framework.
F. Implementation across UK & supply chain focus
- The Bill’s territorial extent is the entire UK. (GOV.UK)
- The focus on supply-chain risk is strong: recognising that it’s not only the “operator” but the suppliers and service providers who need to be addressed.
3. Who is in scope / Who will be affected



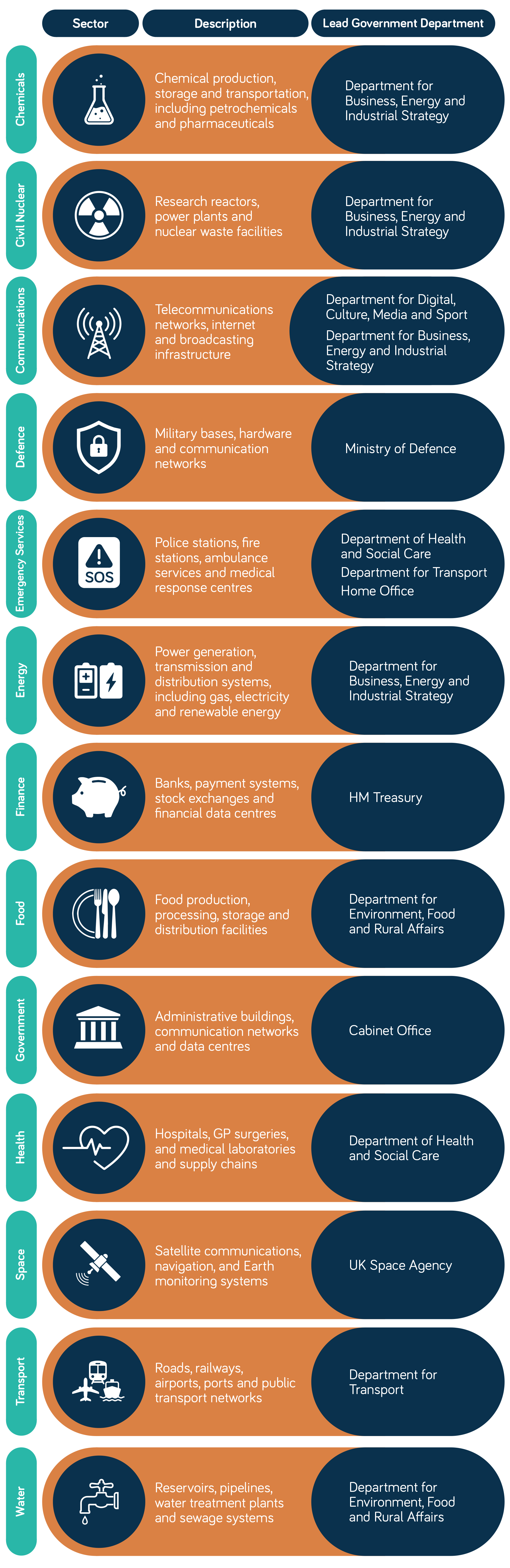

Likely to be in scope
- Operators of essential services (OES) such as transport, energy, water, health, digital infrastructure. (GOV.UK)
- Digital service providers (RDSPs), especially cloud services, data centres, service providers to critical infrastructure.
- Managed service providers (MSPs) and suppliers that have access to or provide services for essential infrastructure or digital backbone. (Estimated 900-1,100 MSPs). (GOV.UK)
- Supply-chain companies designated as “critical suppliers” by regulators under the regime.
Exemptions / smaller firms
- The policy statement emphasises proportionality: the government intends not to bring in “all small businesses” but to target the higher risk entities. (GOV.UK)
- However, even if a firm is “only” a supplier to a critical service, they may end up being designated and thus captured.
What type of incidents will matter
- Incidents that affect confidentiality, integrity or availability of services.
- Possibly ransom events, supply-chain compromise, third-party breaches. (Though final thresholds still to be confirmed.)
4. Key timelines & process
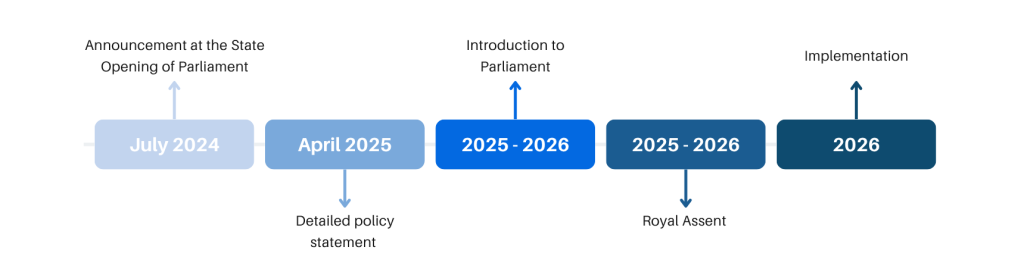



- The Bill was announced in the July 2024 King’s Speech. (GOV.UK)
- A key policy statement was published on 1 April 2025 outlining the measures. (GOV.UK)
- The Bill is expected to be introduced to Parliament in 2025. (GOV.UK)
- After introduction there will follow the usual legislative stages: first reading, second reading, committee stage, report stage, third reading, then possible House of Lords and Royal Assent. (Wikipedia)
- Implementation and enforcement: While exact commencement dates are not yet final, firms in scope should assume they will need to comply soon after passage.
5. Implications & what organisations should do now





Implications
- Firms that provide services to critical infrastructure or are part of essential services supply-chains will face mandatory duties rather than voluntary best-practice.
- Stronger regulatory oversight, reporting deadlines, designated supplier obligations will increase administrative and compliance burdens.
- Penalties for non-compliance (though not fully specified yet) are likely to be significant — including fines and reputational damage.
- Supply-chain resilience and risk-management will become core: you might be regulated even if you’re not the “top-tier” operator but you are a supplier.
- Firms will need to engage with regulators and perhaps adapt to new standards such as the NCSC Cyber Assessment Framework.
- Boards and senior leadership will have greater responsibility: cybersecurity is increasingly a “business risk” issue.
What to start doing now
- Map your services: Understand if you are part of or serving an “essential service”, “digital service”, or supply-chain to such. If so, assume you are in scope or could become so.
- Identify MSPs/suppliers: If you are a managed service provider, or you provide services into critical infrastructure, begin assessing exposure now.
- Review incident management & reporting: Ensure you have robust incident response, can detect incidents promptly, and have reporting mechanisms in place. Why? Because the Bill signals shorter reporting windows.
- Assess supply-chain risk: Identify your key suppliers, and ensure they themselves have good cyber hygiene. Document your supplier risk approach and portfolio.
- Governance and leadership engagement: Ensure your board/senior management are aware of the Bill and that cyber-risk is treated as a business-risk.
- Benchmark against frameworks: Consider aligning with the NCSC Cyber Assessment Framework or other recognised standards to mitigate risk.
- Monitor regulatory developments: As the Bill passes through Parliament, secondary legislation (codes of practice, delegated powers) will fill in many of the detailed requirements. Staying ahead gives you a competitive and compliance advantage.
6. Strengths & Potential Gaps / Critiques
Strengths
- Moves the UK’s regulatory regime forward to meet current threat landscape rather than relying on legacy frameworks.
- Strong focus on supply-chain and managed-service providers — addressing a known weak point in cyber-defence.
- Powers to make the regime adaptive (via delegated legislation) means future threats can be addressed more quickly.
- Recognises the business/economic dimension of cyber-resilience, not just security for its own sake.
Potential Gaps / Things to Watch
- The full detail of what constitutes a “significant incident”, what reporting thresholds apply, and how enforcement works is still to be finalised. As one commentary puts it: “The Bill as yet has no information on any punishments for non-compliance …” (Wikipedia)
- There may be cost and regulatory burden implications for smaller firms if not scaled appropriately — balancing risk vs burden will be important.
- Firms outside the traditional “critical infrastructure” footprint may wrongly assume they are safe; the supply-chain focus means impact may be broader.
- The timeline for implementation and how quickly firms will be expected to comply may be challenging, especially for those needing significant upgrades.
7. What this means for organisations outside the UK (or with UK links)
- Even if you are not headquartered in the UK, if you supply services to UK-based essential or digital services, you may fall in scope (especially if you are a supplier to a UK-based regulated entity).
- If you operate globally and include a UK footprint, you will need to ensure compliance for the UK part of your business — and this may drive global change/synchronisation of standards.
- It may lead to alignment or divergence with equivalent EU regulation (such as the NIS 2 Directive) — so multinational organisations need to track both regimes.
8. Summary
In summary, the Cyber Security and Resilience Bill is a major step by the UK government to modernise the legal framework around cyber-security, elevate compliance, enhance supply-chain protections, and increase regulatory powers. The shift is from voluntary/residual regulation to a more assertive regime, recognising the higher stakes of cyber-attacks in the digital era.
For organisations, the message is: don’t wait. Even though the Bill is not yet law, the writing is on the wall. If you are part of an essential service, digital service provider, MSP, or supplier to such, you should be preparing now.
Here are case studies and expert commentary on the UK Government’s new Cyber Security and Resilience Bill (CSR Bill) — showing how real-world organisations might be affected, how similar laws have worked before, and what security leaders and analysts are saying.
CASE STUDY 1: NHS Trusts — Lessons from the 2022 Ransomware Incident
Background:
In 2022, an attack on an NHS software supplier (Advanced) disrupted patient services across multiple trusts, including access to 111 services. The root cause wasn’t the NHS itself — it was a third-party vulnerability.
How the CSR Bill would apply:
- Under the new Bill, Advanced (the supplier) would likely be designated as a “critical supplier”.
- It would face mandatory cyber resilience requirements and faster incident reporting (potentially within 24 hours).
- Regulators could impose compliance audits or fines if it was found that baseline protections (patching, segmentation, access control) weren’t maintained.
Outcome & Lessons:
- The NHS had to revert to manual systems for several weeks.
- Under the Bill, such incidents could trigger regulatory intervention and risk mitigation orders.
- It highlights why supply-chain accountability is a major theme — “you’re only as strong as your weakest vendor.”
Expert comment:
“This Bill is essentially a direct response to events like the NHS supply-chain breach. It recognises that resilience cannot end at the firewall — it must extend to every connected partner.”
— Dr. Ian Levy, former Technical Director, NCSC
CASE STUDY 2: Managed Service Providers (MSPs) — Expanding Regulatory Reach
Background:
A UK-based MSP serving 200 SMEs suffered a remote management platform breach in 2023. The compromise cascaded into client networks, encrypting hundreds of endpoints.
Under the CSR Bill:
- The MSP would now be within scope of regulation, even though it didn’t serve “critical national infrastructure.”
- The Bill explicitly mentions 900–1,100 MSPs expected to come under oversight.
- It would require compliance with NCSC’s Cyber Assessment Framework, proactive audits, and stricter incident reporting.
Impact:
- The MSP sector will see higher compliance costs but also stronger client confidence.
- Those who adopt frameworks early could use compliance as a competitive advantage — similar to how ISO 27001 certification became a market differentiator.
Industry comment:
“Managed service providers are the new soft underbelly of the UK’s digital ecosystem. This Bill finally gives regulators the teeth to ensure that the companies we entrust with access to hundreds of networks are properly secured.”
— Jamie Akhtar, CEO, CyberSmart
CASE STUDY 3: UK Energy Grid Operator — Scenario on Supply-Chain Designation
Background:
A regional energy operator depends on multiple subcontractors for digital control systems and maintenance. One of these vendors introduced a vulnerability through an unpatched IoT control interface.
Under the CSR Bill:
- The vendor could be designated a “critical supplier”, bringing it under direct regulatory scrutiny.
- Both the energy operator and vendor would be required to jointly manage supply-chain risk and demonstrate resilience testing.
- Regulators could issue Improvement Notices or Compliance Orders if weaknesses were not addressed.
Outcome:
- Potential reduction in systemic vulnerability through mandatory auditing.
- Encourages deeper collaboration between main operators and suppliers — sharing risk data and standardising security protocols.
Policy analyst view:
“By regulating critical suppliers, the Bill corrects a blind spot that’s plagued cybersecurity for a decade. But success will depend on how proportionately it’s implemented — overreach could stifle smaller vendors.”
— Samantha Green, Policy Fellow, Chatham House
CASE STUDY 4: Local Government — Ban on Paying Ransoms
Background:
Several UK councils have paid ransom demands following cyberattacks that encrypted data and disrupted citizen services.
Under the CSR Bill:
- Public bodies would be prohibited from paying ransoms to hackers.
- Instead, they must have incident response and recovery plans certified by regulators.
- Failure to comply could result in financial penalties or leadership accountability.
Outcome:
- Forces investment in resilience rather than ransom payouts.
- May cause temporary disruption for councils that have underinvested in backups or response frameworks.
Public policy perspective:
“The ransom-payment ban is a moral and economic decision. Paying criminals fuels the industry. The Bill ensures the public sector can’t take the easy way out.”
— Lord Bassam, Shadow Home Office Spokesperson
CASE STUDY 5: Cloud Infrastructure Provider — Cross-Border Compliance
Background:
A US-based cloud services firm hosts data for multiple UK government departments. The firm operates globally but stores backups in EU data centres.
Under the CSR Bill:
- The UK operations would fall under the “digital service provider” category.
- The firm would need to comply with UK-specific incident reporting and security standards, even if already compliant with EU NIS2 Directive.
- The Bill’s extraterritorial reach could force global firms to harmonise UK and EU compliance processes.
Outcome:
- Aligning UK and EU standards could simplify global compliance but increase admin load.
- May prompt cloud providers to open UK-specific sovereign regions for data hosting.
Analyst note:
“This Bill nudges global cloud giants to take UK sovereignty seriously. Expect to see more ‘UK-only’ data regions emerging as a result.”
— Dr. Rebecca Frost, Head of Policy, TechUK
Expert & Industry Commentary
1. National Cyber Security Centre (NCSC)
“The Bill will make resilience a business necessity, not a voluntary aspiration. It will give regulators stronger oversight and ensure faster responses to incidents.”
2. Confederation of British Industry (CBI)
“While we support the objectives, clarity on cost recovery and compliance expectations for SMEs is vital. A one-size-fits-all model could strain smaller providers.”
3. Federation of Small Businesses (FSB)
“We urge proportional enforcement. Many small IT suppliers serve large clients but lack the resources of major MSPs. They need support, not punishment.”
4. Cybersecurity Researchers (Oxford Internet Institute)
“The Bill represents a shift from reactive cybersecurity to proactive resilience. But without sufficient investment in training and NCSC capacity, enforcement could lag behind intent.”
Overall Takeaways
| Theme | Impact | Commentary |
|---|---|---|
| Supply-chain accountability | Expands legal responsibility to MSPs and suppliers | “Every vendor is now part of the security perimeter.” |
| Incident transparency | Shorter reporting times, stricter disclosure | “The 24-hour window forces operational readiness.” |
| Ransom bans | Stops public funds going to criminals | “It’s a deterrent policy, not just security.” |
| Regulator powers | Cost recovery, compliance audits | “Regulators finally get teeth — but must use them wisely.” |
| Global impact | Affects international cloud and tech firms | “UK compliance could become a new gold standard in Europe.” |
Final Comment
The Cyber Security and Resilience Bill is being hailed as the UK’s most comprehensive cyber legislation since the NIS Regulations of 2018.
It pushes cybersecurity from the IT department to the boardroom, mandating resilience, accountability, and transparency across the public and private sectors.
As one security strategist put it:
“The CSR Bill is less about punishment and more about preparedness — the UK is saying: we won’t wait for the next crisis to learn our lesson.”
— Martin Hodgson, CISO, BT Security



